Write-up of the challenge “Forensic – Where Is My Purse?” of Nuit du Hack 2018 CTF qualifications.
The weekend of 03/31/2018 is pre-qualification for the Nuit du Hack 2018 as a Jeopardy CTF. Having had the opportunity and the time to participate with some colleagues and friends, here’s a write-up resolution of the challenges which we could participate.
- Category: Forensic
- Name: Where Is My Purse?
- Description : Helps an important person to find the content of his numeric purse.
- File : whereismypurse.7z (2.74GB – 83cf33c0cb86457c929237a1b1d8763fad1a28734b987c0f69b9d9f6b66e85db)
- Points : 200
The challenge’s goal is to access to a wallet content from a virtual machine and a memory dump provided in fournis dans l’archive 7z.
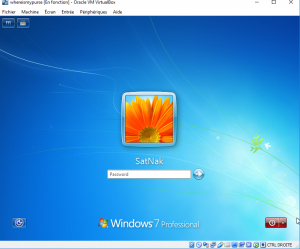
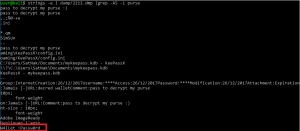
To run VM, we create a new machine in VirtualBox and we attache the disk file whereismypurse.vdi to it. Once run, we see a Windows 7 system protected with a password :
One possible option is to use a tool such as konboot to bypass Windows authentication. A loading of the tool’s ISO at system startup allows us to log in as user SatNak without password.
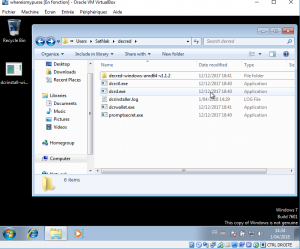
On the desktop, we can see an executable named dcrinstall-windows-amd64-v1.1.2.exe. A quick search on the web tells us it is a tool related to the crypto currency « Decred ». The executable deploy the tool in the directroy %USERPROFILE%\decred\ :
The tool’s binaries are likely to provide access to the wallet mentioned in the description of the challenge. After playing a little with these executables, we note that a secret is necessary to continue the challenge.
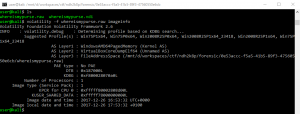
It is assumed that this secret can be retrieved from the memory dump provided in the 7z archive. Let’s use Volatility to analyze this one:
The list of running programs or commands tells us that a KeePass vault is launched:
This process can be extracted using the following command:
$ volatility -f whereismypurse.raw --profile=Win7SP1x64 --dump-dir=dump memdump -p 2212
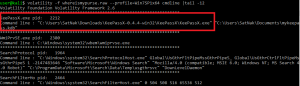
A simple search for strings in the contents of this dump allows us to find the password contained in the Keepass vault:
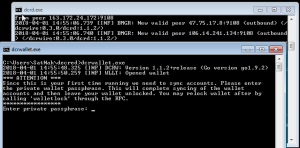
Back in the VM, we run the executables dcrd.exe and drcwallet.exe and enter the password found previously when prompted:
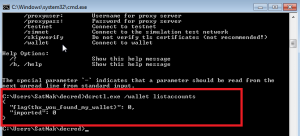
Once the password is validated, dcrctl.exe allows us to access the content of the Wallet and find the flag:
Thanks to Timothée MENOCHET for the write-up ! 🙂
Greeting to the whole team ! 🙂