Write-up of the challenge “Network – Kebab STO” of Nuit du Hack 2018 CTF qualifications.
The weekend of 03/31/2018 is pre-qualification for the Nuit du Hack 2018 as a Jeopardy CTF. Having had the opportunity and the time to participate with some colleagues and friends, here’s a write-up resolution of the challenges which we could participate.
- Category: Network
- Name: Kebab STO
- Description : The challenge consists in finding the flag into a network capture.
- URL : tcp://kebabsto.challs.malice.fr:8888/
- File : kebabsto.pcapng (149.66kB – c714bd030c959275df197ca7a392c21d3f68fa9fd6a161ab7ffa5e896ef7f0eb)
- Points : 350
This challenge is about a pcapng analysis using a TCP service kebabsto.challs.malice.fr:8888 too.
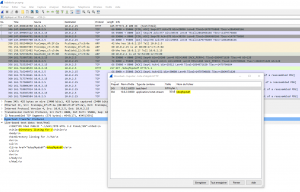
Opening with Wireshark the kebabsto.pcapng, and try to export HTTP objects :
The first object is the HTML source code of an Apache “index of” referencing one file called “kdsqfkpdsdf” and the second is this file itself.
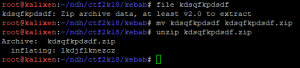
The “kdsqfkpdsdf” file is a ZIP archive, extract it :
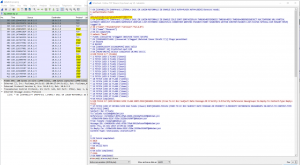
Before the analysis of the ZIP content, continue on the initial PCANG file. There are several IMAP/SMTP exchanges :
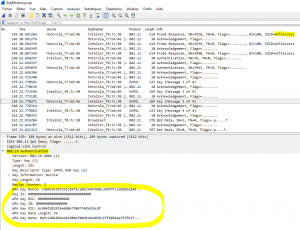
These IMAP exchanges are authenticated :
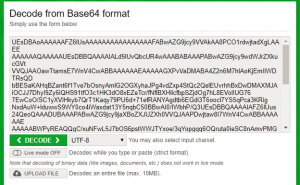
AHRvbWF0ZUBkZWJpYW4ueW8AdG9tYXRlMTIz Base64 decode : tomate@debian.yo:tomate123
Plus, an attachment is present in one email (encoded as Base64) :
We can retrieve this attachement via online service :
This new file is a ZIP archive too with 2 files :
- docs/pubkey.pem : an RSA 1024b public key. none of RSA attack technics work on it (factordb, Wiener, etc.)
- docs/cipherText : a big integer number as ciphertext
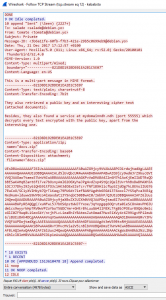
The email content from the PCAP is also interresting. There is precision about the TCP 8888 service :
They also retrieved a public key and an interesting cipher text
(attached documents).Besides, they also found a service at mydomainndh.ndh (port 55555) which
decrypts every text encrypted with the public key, apart from the
interesting one.
There is a little mistake, it’s not the 55555 port but 8888 in reality. So this service implements the pubkey.pem to decrypt ciphertext submited. Try it with the content of “cipherText” :
72873754879996948796542757182427480866384878894019674005699447004829908491467629529161961884224325941110935083467870715412599916138560976722953815670278067115980556377912852138532905866093650699880301357138301236748217037629036311469031537013958415575513723738671978421707050599317605219729945496472798064172
Yeah ! It seems to be a password. But where and when can we use it ?
Go back earlier to the analysis of the kdsqfkpdsdf file retrieved from HTTP exchanges. It’s a ZIP containing another PCAP file :
Load it in Wireshark :
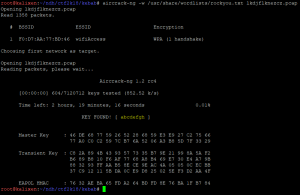
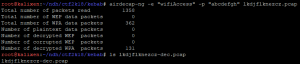
Several Wifi-WAP encrypted exchanges from an access-point called “wifiAccess” are available. Authentication requests too. We can try to break the WPA passphrase via the rockyou.txt wordlist :
Bingo, the WPA passphrase is “abcdefgh”, we can now decrypt this PCAP file to see it’s real content :
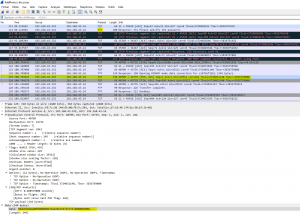
In this decrypted PCAP file, we can get :
- Several TCP exchanges (but only ACK) ;
- IMAP/SMTP authenticated exchanges (new credentials fromage@debian.yo:fromage123);
- FTP exchange with content as hexadecimal value :
We recreate the file send through FTP with a little Python script and analyze it :
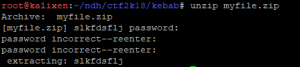
Another ZIP file ! But this one is password protected… We can try all credential retrieved (tomate123, fromage123, the WPA key, the password unciphered via the TCP 8888 service) :
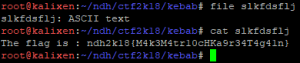
YES ! It was the password from the TCP service “Th1s1s2P@ss_W0rd%M0f0”. A final file is extracted with ASCII content : slkfdsflj.
Greeting to the whole team ! 🙂