Write-up of the challenge “Crypto – One too many” of Nuit du Hack 2016 Wargame
The weekend of 02-03 july 2016 is the WARGAME of the Nuit du Hack 2016 as a Jeopardy CTF. Having had the opportunity and the time to participate with some colleagues and friends, here’s a write-up resolution of the challenges which we could participate.
- Category: Crypto
- Name: One too many
- Description : We encrypted both parts of the flag with our revolutionary two-time-pad technique! Are you able to recover it?
- URL : http://static.wargame.ndh/one_too_many_1.png and http://static.wargame.ndh/one_too_many_2.png
- Points : 100
tl;dr : one_too_many_1.png XOR one_too_many_2.png (convert tool on kali)
Two PNG images are provided to us for this challenge:
The technique of “One-Time-Pad” was used to encrypt these images, and the key is identical between the two ciphers (two-time-pad).
The following relationship follows:
one_too_many_1.png = one_too_many_1_original.png XOR OTP one_too_many_2.png = one_too_many_2_original.png XOR OTP one_too_many_1.png XOR one_too_many_2.png = one_too_many_1_original.png XOR one_too_many_2_original.png
A simple Google search on a fast method to XOR two images, brings us to this topic, which details the use of the command “convert”. The methodology is applied:
convert one_too_many_1.png one_too_many_2.png -fx "(((255*u)&(255*(1-v)))|((255*(1-u))&(255*v)))/255" one_too_many_flag.png
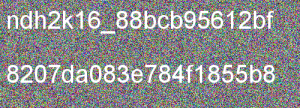
And the flag is displayed : ndh2k16_88bcb95612bf8207da083e784f1855b8
Thank you to all the team of the NDH2K16 for this event and for the whole organization!
Greeting to nj8, St0rn, Emiya, Mido, downgrade, Ryuk@n and rikelm, ? // Gr3etZ